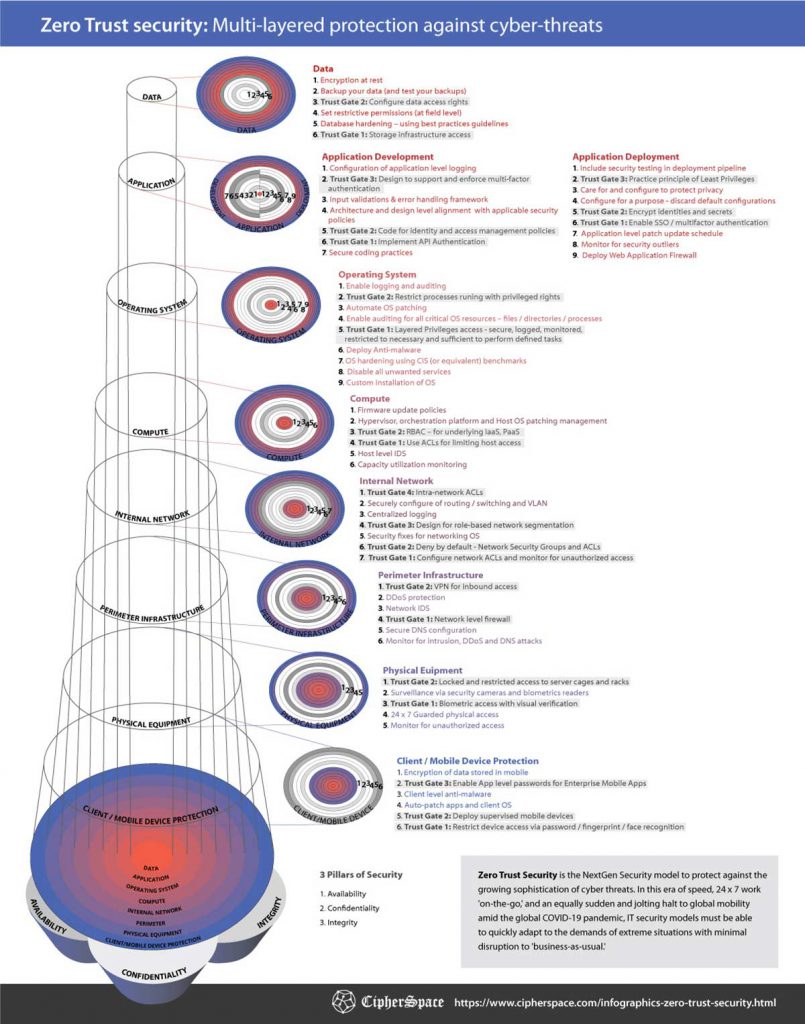
Defense in Depth: Security layers to deploy Zero Trust
This infographic shows how the Zero Trust Model uses a combination of ‘Trust Gates’ and ‘Defense-in-Depth’ at every layer of security to protect Confidentiality, Integrity, and Availability of your most valuable asset — Data.
Download the print quality Zero Trust Security Infographic:
Zero Trust Security is the NextGen Security model to protect against the growing sophistication of cyber threats. In this era of speed, 24 x 7 work ‘on-the-go,’ and an equally sudden and jolting halt to global mobility amid the global COVID-19 pandemic, IT security models must be able to quickly adapt to the demands of extreme situations with minimal disruption to ‘business-as-usual.’
The Zero Trust Security Model doubles-down on establishing trust at every layer of the deployment stack. Access is granted only after verifiable trust is formed at every level of access,
- User identities are checked, and credibility is established for all of the following access types:
- Applications
- Operating Systems
- Compute Infrastructure
- Networking Infrastructure
- Device identities are challenged and verified
- Applications and APIs requesting access are substantiated
- Identities of people requiring physical access are matched against a pre-approved database of biometrics
- Network-level trust criteria are chalked out and implemented with “Why should I trust you?” as the front and center question.
The Zero Security Trust Model is a paradigm shift from the traditional castle and moat model. It is highly effective in protecting Confidentiality, Integrity, and Availability of your Digitial Assets – irrespective of the location of the workforce.
LinkedIn Feedback
For a step-by-step overview of these layers, check out our Zero Trust Security video:
LinkedIn post by Dan Williams – Senior Security Infrastructure Engineer
S Vikravel – Solutions Architect (Cloud / Devops)
Interesting 👌
Harold Walker
I like this! Pretend they are already inside and build defense inside out!
Michael Maccini – Founder/CEO at WVG Ltd, Inc.
Dan is the Man.
Ateesh Bhat – Security Delivery Specialist C|EH v10 | PA Cortex-XDR | Splunk Admin
Thank you, Dan Williams.
Randolph Rosenberg – Principal Security Architect – Group Digital Platforms at TuI
Good find, reposting. Thanks Dan Williams
Randolph Rosenberg – (Principal Security Architect – Group Digital Platforms at TUI)
Good find, reposting. Thanks Dan Williams
Jay Ribeiro – (ATF Chief Information Security Officer (CISO))
Is it still zero trust if you’re discussing perimeter centric protection or layer (trust zones — VPN, etc.)? What’s the point of zero trust?
Jigar Shah – Product Management & strategy | Customer Success |Product Marketing | Pricing | Business Development| Revenue Growth
Dr, Jay R. The way I interpret trust is akin to measures taken and challenges presented before an individual is allowed to access an asset stored in Maximum Security Facility, I’m no expert in workings of such operations in military grade settings, but I would assume that verification and unambiguous identity establishment would be done at each and every level as one approaches closer to the asset.
With that analogy in mind, Zero Trust exists to gain a high degree of confidence in the process of answering the question ‘To trust or To Not Trust?’, and hence it must be comprehensive and at every layer that makes the perimeter around the valuable asset.
It would be an engaging read for me (and I’m sure for others too), if you would like to share what in your opinion is the point of Zero Trust?
Dr, Jay R. The graphic supports importance of trust at every layer, even if the some of layers have moved outside of traditional ‘zone’.
Jay Ribeiro
Jigar Shah that makes sense. Probably label it as Defense in Depth is my recommendation as more appropriate. Zero trust to me is mostly at layer 7 and identity and NOT zones where you can trust. Zero trust is removing trust but verifying. But anyways, good discussion. Hope it stimulates your readers minds. Thanks for sharing.
Jigar Shah
Dr Jay R. Thanks for sharing your thoughts, appreciate it.
David O’Berry – CISSP-ISSAP, ISSMP, CSSLP, CRISC – Cyber-Security uRuG because self-proclaimed “Gurus” never are no matter what they say…
Beastmode graphic. Missing a few things but I appreciate the way they laid it out.
Jigar Shah
David O. Thanks! It would be interesting to know ‘a few missing things’. It will be a welcome addition to the collective brain of InfoSec community.
HT Cleo Huggins – the artist of this infographic!
David O’Berry
Jigar Shah You folks did astronomical work here to lay this out. I will send you some thoughts but suffice to say it’s one of the single best illustrations of this topic myself and several colleagues have seen. Kudos to you Jigar and to Cleo. 🙏🙏
Jigar Shah
David Thank you! 🙏
Cleo Huggins – Designer
Thank you David O. Please send your thoughts, it would be great to make this more beast-worthy!
Marlon Manborde – Service Desk Analyst at Inergi / Capgemini
Thanks for sharing this Dan
Petar Lachkov – A.A.S. Information Security | LPIC | Linux+ | VCA
This is very in depth thank you for sharing
Kyle Jones – System Support Administrator at Security Service Federal Credit Union
This is amazing
Mark Ward – IT Operations | Software Developing | Automated Systems | Information Security | Databases | IT Support
Like an onion. It has many layers.
Kannan A – Consultant at Standard chartered global business services private ltd
Thank you for this post, interesting to read further in detail…
Karen B. – Founder at CyberAdeptness LLC
This is why I continue to emphasized the importance of addressing OSI Layers separately during an assessment process. They are all unique and distinctive in nature across the board. Especially within Cloud environments.
Certainly- there’s many other items that must be addressed- but they won’t all fit in a graphic and they are unique to each organization. Grasping the UNIQUENESS of each organization is essential.
Thanks for sharing- ERM/SSE are key for this to function properly.
Md Zahid Hasan – Web Developer & WordPress Expert
formative graph
Manisekaran Chandramohan – Sr Technical Architect – ✔️Be practical, ✔️be secure, ✔️be agile, be effective Deliver.
Fantastic infographic. Thanks for hard work ~ 🙂
Andy Jenkinson – Group CEO CIP The Cryptography Governance, PKI discovery and management experts for pre and post Quantum security.
Thanks Dan. There’s quite a lot missing!
Missing Code Signing and use of robust Cryptography.
Operating System – Missing Certificate and Key Discovery.
Computer layer – Missing Key Management for Encryption Services.
Internal Network – Missing strong authentication using Certificates for all Network Services that can use Certificate based authentication.
Perimeter Infrastructure – Missing DNSEC or Certificate and Key Management thereof, likewise DKIM for Email relay Servers or Certificates and Keys for VPN authentication.
That’s just a cursory glance.
Gurdit Sohal – Senior Consultant at Deloitte UK
Hi – I don’t think it should be seen as all encompassing – but 1) More as quidance, and 2) as a first step.
Andy Jenkinson
Gurdit Sohal I read Zero Trust which if it doesn’t include my list it’s only part zero trust, so it’s not!
Jigar Shah
Andy Jenkinson Thanks for reviewing this Infographic in detail and providing feedback. Some of the stuff you mentioned are covered at higher level, for example: Secure coding practice should include code-signing, and secure DNS configuration should include DNSEC. Your list has good pointers and I’m sure will act as a specific guidance to those who choose to use this infographic like how judges use law, as a guidance to interpret and implement for a particular case.
Gurdit Sohal
🙂
Andy Jenkinson
Jigar Zero Trust can never be achieved without proper PKI and is the very foundation of Trust, not optional! It is misleading to ever suggest otherwise.
Jigar Shah
Andy Jenkinson agree to disagree. The way I look at it, Trust is a concept, and PKI is ‘a way’ to achieve it and helps elevating confidence, but not the only option. Trust, which is a subset of IT security, which in turn is a subset of corporate level Risk Management, is about managing the risk and reducing it to a level that is acceptable for ‘the business’ that is implementing it by staying within the constraints of ‘cost, feasibility and regulation’. For one, sufficient trust could be a achieved (given all other factors) using strong password, for another MFA could be must!
To eliminate risk is next to impossible, what is achievable is reduction of risk to a level that is acceptable to all stakeholders to continue to operate business functions.
Trust, then, is about measures taken to unambiguously and securely establish identity of the entity asking for access, irrespective of the technology solution being used.
Korinne M. Jackman – I’m passionate about cybersecurity.
Jigar Shah, exactly. It’s about balancing the needs and goals of the organization against their particular risk appetite, then building their program based on those parameters.
Andy Jenkinson
Zero trust has zero chance and currently is a nice line and nothing more until PKI is recognised and properly managed. At foundation level, Zero trust is being built on sand and the tide comes in daily. PKI is not an option, it is fundamental. Any security, zero trust included, must include PKI or is totally misleading.
Vishal Patil
I do agree there some security measures are missing like email security spam mail. PKI , DMARC, SPF, DKIM etc
David O’Berry
Let me be clear and state I really can’t stand the term “Zero Trust” for any number of reasons not the least of which is the ambiguously defined aspect of the construct.
David O’Berry
Andy Jenkinson How are you discounting other methods of achieving the requisite level of trust for the resources available? I don’t see how the absence of a full PKI implementation demeans a solid zero trust solution based on the needs of the business. I realize we may have a hammer and nail thing here based on what you do but I am genuinely interested why you believe what you do.
Andy Jenkinson
Thanks David. PKI was designed to authenticate and assure every user, device, software and so on. In the last 20 years , no matter how good security or defences have been, if the certificate has expired, been compromised, fake, bogus or stolen, it will undermine every form of security that has any relation or dependency on it. Its like flicking the switch in your house expecting the light to come on when there’s a power outage
David O’Berry
Andy Jenkinson I mean I understand PKI fully I am just not sure a full PKI implementation is required depending on the business requirements. Maybe we are saying two different things because I do recognize that certs are needed etc but full Enterprise PKI is a fairly heavy lift at times and can be overkill in some circumstances. Does that make more sense as to what I am saying so that we can set the baseline for the discussion?
Andy Jenkinson
David O’Berry knowing what your PKI looks like, what certs are deprecated, expiring and about to expire are critical zero trust or otherwise.
Vishal Patil – General Manager- IT & Automation at Serum Institute of India Pvt. Ltd.
Great…it is awesome and easy to understand.
ReZa AdineH – SOC & CSIRT Architect, Adviser, Consultant, SIEM Engineer,Threat Intelligence Expert, Author & Instructor
great
Anas Anwar – Science never sleeps
Amazing 👌🏻
Gurdit Sohal – Senior Consultant at Deloitte UK
Thank you for sharing, Dan- much appreciated.
Dipen Shah – Senior Application Security Engineer at Staples
This is awesome Dan!
Michael R. – Chief Engineer & Solutions Architect, Technical International Programs
This is excellent Dan. Thank you!