“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
— Stéphane Nappo
IT Security – defined as measures taken to protect an Internet-connected computer or computer system against unauthorized access or attack.
Cyber Security has become a major challenge, if not one of the greatest challenges of our times. Hackers are constantly updating attack vectors and seeking new ones.
Systematic coordinated attacks by hackers and in some cases state-sponsored organizations to spy on individual and organizational data are launched to steal identities and intellectual property or to simply render your servers unavailable to you and your customers. Theft or loss of data can impact your business for years.
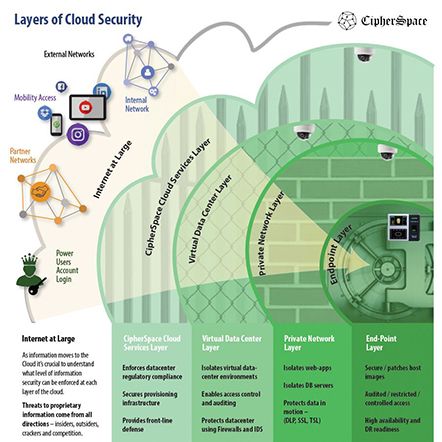
We take a holistic approach to security by deploying best practices and tools at each layer of your infrastructure to secure the data served by respective layers.
Core components that round up our managed security services:
- Managed Firewall
- Managed VPN
- Vulnerability Scanning and Detection
- Log Monitoring
- IDS / IPS
- Threat Monitoring and Reporting
- Incidence Response and Recovery
Security – Why is it so hard to get started?
5 Steps for Organizations of Any Size – Use these steps to establish a solid foundation for developing and implementing IT Security Controls, and Policies and Procedures.